Why in the News?
MeitY, CERT-In, and cybersecurity firm SISA jointly launched a whitepaper titled "Transitioning to Quantum Cyber Readiness" to prepare for disruptive potential of quantum technologies, especially in cybersecurity.
More on the news
- The whitepaper warned that Quantum computers pose a serious threat to current encryption algorithms by breaking asymmetric cryptographic protocols such as Rivest-Shamir-Adleman (RSA).
- Quantum computers can solve complex, intractable mathematical problems - and perform tasks in machine learning, optimization, and logistics - orders of magnitude faster than conventional computers.
- As per the paper, any data requiring protection beyond 2030 should be considered at immediate risk.
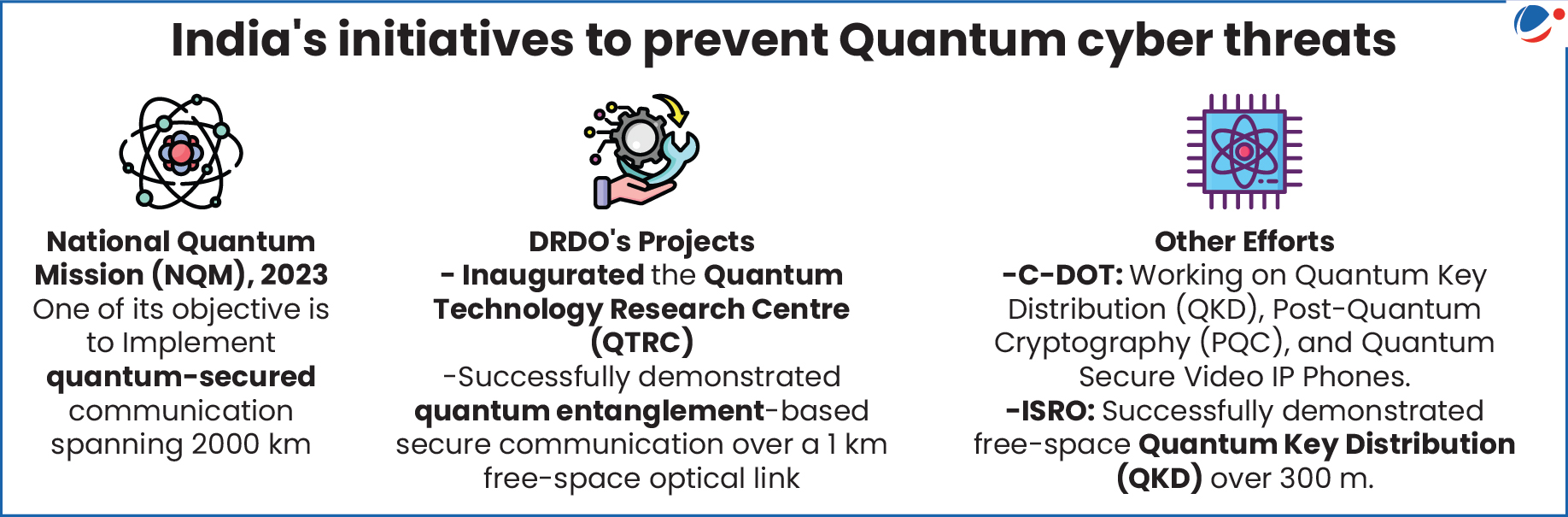
Cyber Threats related to Quantum Technology
- Harvest Now, Decrypt Later (HNDL) Attacks: These attacks involve adversaries collecting and storing encrypted data today with the intention of decrypting it once quantum computers become capable of breaking current cryptographic systems.
- Secure channel decryption: Quantum computing can break encrypted network communications and "listen in" on sensitive conversations like defence communications.
- Signature impersonation: Quantum computing can enable attackers to forge digital certificates, enabling malware distribution and targeted phishing.
- New "Zero-Day" vulnerabilities: This includes the potential for yet unknown quantum algorithms to break existing cryptographic systems and challenges associated with transitioning to quantum-resistant cryptography.
Way Forward: Roadmap for Quantum Cyber Readiness recommended by whitepaper
Area | Recommendations |
Foundational Assessment & Strategic Planning |
|
Technology Readiness & Capability Building
|
|
Phased Organizational Rollout
|
|
Resilience, Monitoring & Futureproofing
|
|
Conclusion
The quantum revolution is inevitable, but organizations that act decisively and strategically will not only protect their data from quantum risks but also lead the way in shaping a quantum-resilient future.




